Index of articles
Click open the Index headers below to browse FAQ
Our support articles address the most common issues we deal with “in the field” about Windows, Microsoft 365 Business, web server support, and web design. Click open the accordion sections below to look for self-serve help. Often, issues rely on a knowledge of IT concepts and language. Also, Microsoft, cPanel, and other software houses featured in these articles often update practice notes and procedures without notice. We review our pages regulalry, however you are advised to contact us for further help about these articles especially concerning issues around sovereign account identity and Multifactor Authentication (MFA).
Microsoft Windows 11
- Windows Pro or Windows Home? A Practical Guide for Business Owners
- Windows Restart vs Shut Down, and Daily Power Management
- Windows 11 System Restore: How to Create and Manage Restore Points Safely
- Windows Recovery drive – why Microsoft recommends it
- Why BitLocker for Small Business Matters
- How to Set Up a New Windows PC to Sign In Directly with a Microsoft 365 Work Account
- Windows 11 Setup Guide: 1. How to Configure Your PC Securely with Microsoft Accounts
- Windows 11: Why One Microsoft Account Isn’t Enough for Home and Small Business Users
- Windows 11 Setup for Privacy-Focused Users: Why Microsoft 365 Business Matters
Microsoft 365 setup, licensing and user management
- How to Set Up Microsoft 365 for a Small Business
- Microsoft 365 Global Administrator: Why Business Continuity needs 2 global admins
- Microsoft 365 Global Administrator: Why You Need a Second Admin and How to Assign Roles
- How to Set Up a New Windows PC to Sign In Directly with a Microsoft 365 Work Account
- How to add a new employee with Microsoft 365 User Onboarding
- How to manage Microsoft 365 when an employee leaves
- How to Set Up Microsoft Authenticator MFA for 365
- How to Back Up MFA Credentials with Microsoft Authenticator Backup
- Microsoft Authenticator iPhone backup
- Locked Out of Your Microsoft 365 Account? Here’s What to Do When MFA Recovery Fails
- What Is a Shared Mailbox in Microsoft 365 and Why Your Business Should Use One
- Change Microsoft 365/email password
- Change Office 365 credit/debit card information
- Why Switching PC Users to Microsoft 365 Sign-In Matters for Small Businesses
- How to Transition PC Users to Microsoft 365 Sign-In and Entra ID
- How to Use Microsoft 365 MailTips to Improve Email Performance
Microsoft 365, Exchange Online and Outlook
- How to Backup Microsoft 365 Outlook Email to a PST File
- Microsoft 365: Outlook Categories
- How to Manage Microsoft 365 Email Signatures
- About Microsoft 365 Outlook templates
- What Is a Shared Mailbox in Microsoft 365 and Why Your Business Should Use One
- How to Use Microsoft 365 MailTips to Improve Email Performance
- How to Use Outlook Sweep to Declutter Your Outlook Inbox
- Email migration from cPanel to Microsoft 365
- How to Use Microsoft 365 Inline Email Archiving
- Create a Microsoft 365 Exchange Online connector
- 2025 Email Security Guide for Business Owners: Avoiding Scams and Attacks
Microsoft 365 configuration and user tips and tricks
- How to Use Folder Color Coding in Microsoft 365 to Boost Productivity
- How to Set Up a Microsoft 365 SharePoint Site for a Small Business
- Create a Microsoft 365 Exchange Online connector
- Configure SPF, rDNS, DKIM, and DMARC for email
The following articles can be found using <Search> or scrolling through our list of articles. Procedures may have changed since and therefore this content is either being eidted or deprecated. So, although we are editing this content, you might still find useful information to help with issues.
- – Exchange Online – room and equipment resources
- – Reset Office 365 password expiration policy
- – Exchange Email – EOP antivirus/spam
- – Exchange Online Protection – EOP
- – Microsoft 365 Exchange Email – data leakage & loss protection
- – Microsoft ActiveSync
Support Articles - cPanel | web server | DNS
- How to Change Your Email Password in Roundcube Webmail
- What Is cPanel BoxTrapper And Why Email Users Should Care
- Email Management in cPanel: Save Space, Cut Costs, and Go Green
- 2025 Email Security Guide for Business Owners: Avoiding Scams and Attacks
- Safeguard your .uk domain names – Nominet
- Email migration from cPanel to Microsoft 365
- How to manage a web site contact form
- How to configure DNS for a contact form
- Configure SPF, rDNS, DKIM, and DMARC for email
- Create a new email address with cPanel
- How to use cPanel Web Disk
- How to back up your web server with cPanel
- Add SPF to your DNS zone record
- Configure DMARC using cPanel
- Configure DKIM in cPanel
- Configure Reverse DNS (RDNS)
- cPanel email account considerations
- Why Authoritative Nameservers Matter for Your Web Hosting Setup
Support Articles - Sitejet web design software

Why Windows Pro Is Better for Small Office: A Practical Guide for Business Owners
Windows 11 - Home edition or Pro?
Many small‑business owners end up using Windows Home without realising it isn’t designed for business needs. This happens for a few reasons. For instance, most small business owners buy their laptops from retailers, and almost all of these machines ship with Windows Home by default. The device looks the same, feels the same, and runs the same apps. Some buyers are not advised adequately to know there is even such a thing as Windows Pro, so it is easy to assume it’s “good enough” for work.
There is also the common idea that a business computer should double as a home computer. It is tempting to use the same device for work, family photos, streaming, and social media. But this creates a hidden risk. A computer that mixes personal and business use is far more likely to be exposed to online threats, accidental installs, and privacy issues.
Microsoft designed Windows Pro for small business users exactly because business devices face higher risks. While Windows Home is built for entertainment and general use, Windows Pro includes additional protections that help keep customer information safe, reduce downtime, and support proper operational security. It also helps you stay aligned with GDPR responsibilities through better data control and stronger security features. Windows Enterprise is fuctionally elevated further and rounds out Microsoft’s strategy for its business-class operating systems.
Even if you never touch advanced settings, these built‑in protections reduce risk and exposure to costly intervention over the long term.
Click open the headers below to learn more about how Windows Pro and Windows Pro are intended to be used. Support options are available for professional assistance. You can return to our Index of Articles by clicking here.
Why Microsoft Makes Two Versions of Windows
Microsoft’s logic is simple:
- Windows Home is built for comfort, entertainment, and incidental daily use
- Windows Pro is built for reliability, security, and work
Business owners deal with invoices, customer details, financial records, tax files, and confidential communications. Losing any of these—through theft, hardware failure, or malware—can be costly. Windows Pro includes tools that protect against these risks automatically, without needing technical knowledge.
Windows Home tries to imitate some business features, but it cannot match the security or resilience built into Windows Pro. For example, Windows Home only includes basic device encryption, while Windows Pro includes deeper, business‑grade protections such as full BitLocker support and professional device‑management options.
Windows Pro: Real‑World Benefits
1. Better protection for your customer data
Windows Pro provides stronger safeguards for your data and is more aligned with GDPR expectations. Full‑disk encryption and professional security controls mean that if a laptop is lost or stolen, your customer and employer information stays protected. Windows Home only offers a basic form of encryption and does not meet business standard compliance.
2. Lower risk when something goes wrong
Windows Pro includes secure isolation tools, such as Windows Sandbox and Hyper‑V. These let you open unknown files or test apps in a safe, temporary workspace. Nothing in that workspace can harm your real computer. Windows Home does not offer this protection.
This feature alone can prevent costly downtime caused by malware, bad installers, or suspicious attachments.
3. Easier for IT support to protect you
Windows Pro allows your IT support to set up safe defaults, manage updates, and protect your device remotely. This is not possible on Windows Home, which lacks proper management tools, domain join, and several security controls.
In practice, this means:
- Fewer interruptions
- Fewer “strange things” happening to your computer
- Faster recovery if something breaks
4. Remote access that actually works
Windows Pro supports Remote Desktop, so you (or your IT support) can access your office computer safely from anywhere. Windows Home cannot act as a Remote Desktop host, limiting remote work and remote support capabilities.Windows Home features “Quick Assist”, and although this does provide some utility, it is a “lite” application designed for home -> home users.
A Business Computer Should Be a Business Computer
A business device is a business asset. Mixing personal use with work increases risk and reduces reliability. When gaming, photos, family streaming, social media, and work all share the same device, problems multiply. This is not debateable. Whether government, or corporate, work computers manage productivity. Combining TikTok, gaming, shopping, etc. within one container poses risks that make equioment more difficult to manage. For this reason alone, small business users endure far more malicious infitration than government or corporate counterprats, even if corporates make headlines with stellar fines.
Keeping work and personal life on separate devices isn’t just safer—it means smoother operation, better reliability, and less prolonged recovery/cost.
Can I update Windows Home to Pro?
Yes. There are two ways to do this, and although the upgrade is simple, we recommend you should ask for us advice about how to plan and prepare for the upgrade.
1. If you have a product key:
In Windows:
- Open Settings
- Go to System → Activation
- Click Change product key
- Enter your Windows Pro key
- Follow the prompts and reboot when asked
Windows will unlock Pro features instantly.
2. Buy Windows Pro through Microsoft Store
If you do not have a product key:
- Open Settings
- Go to System → Activation
- Under Upgrade your edition of Windows, select Open Store
- Purchase Windows 10/11 Pro and it will upgrade automatically
Note – Microsoft 365 Business users are upgraded to Microsoft Windows Enterprise edition on activation of a Windows Pro license.
Summary
Upgrading to Windows Pro does not mean learning new technology. It is Microsoft’s approach to reducing risk, improving resilience, and protecting customer data automatically. For most small‑business owners, Windows Pro silently delivers the security, reliability, and peace of mind you thought you were getting with Windows Home.
If you would like help implementing a Windows Pr update, feel free to get in touch, or use out contact page to organize an appointment which suits your timetable. You can return to our Index of Articles by clicking here

Windows 11 System Restore: How to Create and Manage Restore Points Safely
What Is Windows 11 System Restore?
Windows 11 System Restore is a built‑in recovery feature that protects your PC by taking snapshots of crucial system files, settings, drivers, and registry entries. These snapshots are called restore points. If something goes wrong after installing software, drivers, updates, or after a malware incident, System Restore allows you to roll your computer back to a previous stable state.
System Restore does not delete your personal documents, photos, or emails. Instead, it focuses on parts of the system that can break Windows. Because of this, it is one of the simplest and most powerful safety nets for everyday users.
System Restore is especially valuable when reacting quickly to malware or virus infiltration. If the infection is recent, restoring the system to a point before the attack can help reverse harmful changes and reduce damage. While it is not a replacement for anti‑malware tools, it adds an essential extra layer of protection.
Click open the headers below to learn more about how to enable System Restore. Support options are available for professional assistance. You can return to our Index of Articles by clicking here.
How You Can Check That System Restore Is Enabled
Many users assume Windows 11 System Restore is switched on automatically. Often, it is not. Some OEMs ship devices with the feature disabled, and major upgrades can also turn it off. For anyone who is not IT‑literate, the most important advice is simple:
“Check once a month that System Restore is enabled“
This is how to verify System Restore is operational:
- Press Windows Key and type restore point
- In System Properties, open System Protection tab
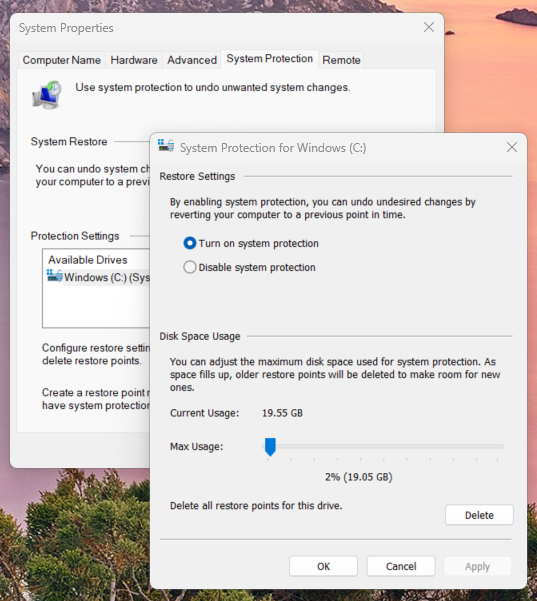
In the screenshot below, see how system restore status is enabled. If protection is off, Windows cannot create restore points automatically — and you won’t be able to roll back when things go wrong.
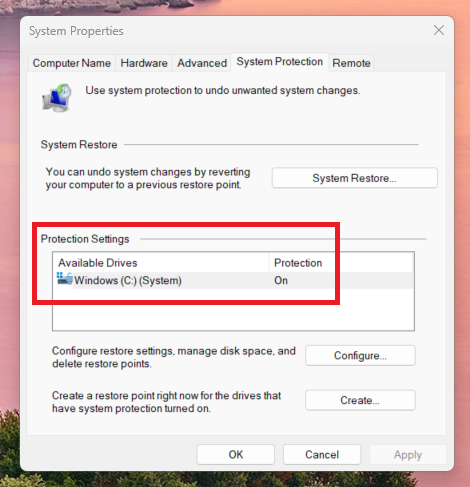
System Restore control panel allows you to enable services, check status, and restore Windows’ last known working state
How to Create a Restore Point in Windows 11
Configure automtatic restore point creation
Creating a restore point in Windows 11 System Restore takes less than a minute and can save hours of recovery work and consequential labour costs. This is how to configure System Restore:
- Press the Windows Key and type restore and click <enter>
- In the System Properties control panel, click open System Protection
- In the System Properties window, select your primary drive (C:) by clicking it to highlight row
- Click <Configure>
- Ensure Turn on system protection is selected
- Confirm that the Max Usage slider has at least 2–5% allocated
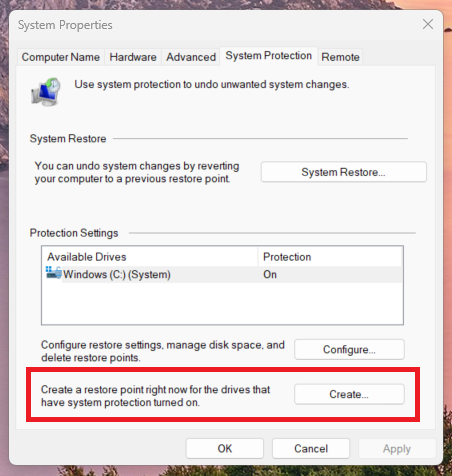
Create a restore point manually
You can also create a system restore point before major changes like:
- Driver installations
- Registry modifications
- Software that affects system behaviour
- Windows feature updates
You can do this by navigating to System Restore control panel described above and clicking the <create> button.
How to recover a Restore Point
Sometimes, a Windows corruption or a malware infiltration needs correcting. Especially if this has happened in the last 2-3 days, you can use System Restore to reinstate Windows to the state it was in before Windows system files were compromised. If your buffer is large enough, you may be able to use earlier system Restore Points, but bear in mind that using old restore points might undo good updates that have been implemented, too.
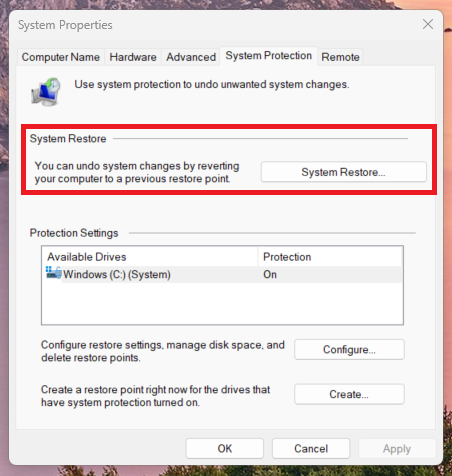
To restore your system:
- Return to the same System Protection window as described above
- Click System Restore
- Choose your restore point
- Follow the on‑screen instructions (see screenshot below)
Best Practices for Using System Restore
To get the most from System Restore, consider these simple tips:
- Keep it enabled: Check periodically that protection has not been turned off
- Create manual restore points before major system changes
- Act fast after malware signs: restoring early increases the chance of reversing harmful changes that antivirus/anti-malware software could aggravate further
- Do not rely on it as your only backup: use OneDrive, external drives, or full‑system imaging for complete protection.
Computer Life expectancy affects recovery options
In larger businesses, the average replacement cycle for computers used for desktop productivity is 3-5 years. Self-employed users demand much more from their computers. This kind of profile is more in line with a corporate power user, whose computers are replaced at 2.5 – 4 years. This is because this kind of useage imposes a heavier computational duty cycle on hardware. While System Restore and Windows Recovery can help mitigate running costs, these kinds of tools cannot perform when hardware has failed or is reaching the end of its duty cycle.
Hot Tip: System Restore is only designed to resinstate a last known working state of your Windows systems files. System Restore does not manage files or user data.System Restore is often more capable of resolving malicious infiltration that antivirus software. However, malicious attacks cause unpredictable consequences which may mean that you still have to resort to your recovery drive (see this article) to correct a serious Windows system problem.
Summary
Windows System Restore is one of the most valuable recovery features built into the operating system. When enabled, it can quickly repair software problems, undo bad updates, and help mitigate early‑stage malware infections. For everyday users and professionals alike, this simple tool offers powerful peace of mind.
If you need help configuring restore points across multiple devices or want deeper protection for high‑value systems, please get in touch, or use our contact page to organize an appointment which suits your timetable. You can return to our Index of Articles by clicking here .

Microsoft Authenticator iPhone backup
Backup Microsoft Authenticator credentials to iCloud
iPhone users can use Microsoft Authenticator iPhone Backup utility to save Microsoft 365 credentials to their iCloud account.
Using Microsoft Authenticator iPhone Backup, you can restore your existing 365 MFA credentials to a new iPhone. Also, you can restore your MFA account if your iPhone’s working MFA settings are corrupted. If you are a 365 tenancy owner or a Global Administrator (GA) ou would need another global administrator (GA) to create new credentials. Without a second GA (see this article about creating a secondary “break-glass” Global Administrator) a Microsoft 365 tenancy owner could lock themselves out of their tenancy. So, backing up 365 Authenticator settings is critically important if you are a tenancy owner.
This article explains how to configure your handset, iCloud, and Microsoft Authenticator iPhone Backup.
Click open the headers below to learn more about Microsoft Authenticator iPhone Backup. Support options are available for professional assistance. You can return to our Index of Articles by clicking here.
How Microsoft Authenticator iPhone Backup Works
On an iPhone, Microsoft Authenticator does not use a Microsoft account for backup. Instead, Microsoft Authenticator relies entirely on Apple iCloud.
There is no backup button inside the app in Microsoft’s version of Microsoft Authenticator for iPhone. Instead, once your iPhone is set up correctly, your MFA settings are synchronised and periodically checked in iCloud and iCloud keychain in the background.
The key requirement is that your iPhone is:
- Signed in to your Apple ID
- Using iCloud
- Using iCloud Keychain
If those conditions are met, Microsoft Authenticator iPhone backup is already working. Click open the next sections to learn how to set up your iPhone.
Important note about your Apple ID – your Apple ID, like a Google, Microsoft (personal) and a Microsoft 365 account – is what is called a sovereign account. Be sure that sovereign accounts are configured with secondary sign-in alternatives, and be sure to verify your record and review your user account contact preferences no less than annually.
Step‑by‑Step: Enabling Microsoft Authenticator iPhone Backup
These steps take about two minutes and only need to be done once. Please read through the workflow before you begin. Also, bear in mind that Microsoft and Apple can change processes from time to time and the workflow may vary depending on your iOS version and iPhone model. In any event, the objective is to enable iCloud, iCloud keychain, and enable iPhone to execute connectivity for Microsoft Authenticator.
1. Confirm You Are Signed In to Your Apple ID
- Open iPhone Settings
- Look at the very top of the screen
- If you see your name, then you are signed in
- If not, sign in with your Apple ID
Microsoft Authenticator iPhone backup needs to be associated with your Apple ID, so this step is essential.
2. Make Sure iCloud Is Turned On
- Open Settings
- Tap your name
- Tap iCloud
- Ensure iCloud is switched ON
Without connectivity to iCloud, Authenticator cannot backup your credentials.
3. Turn On iCloud Keychain (Most Important Step)
- Go to Settings → your name → iCloud
- Tap Passwords & Keychain
- Turn iCloud Keychain ON
iCloud Keychain securely stores your 365 MFA settings so that they can be retreived later. If you store Microsoft Authenticator credentials for other services, you can back these up too.
4. Allow Microsoft Authenticator to Use iCloud
- Go to Settings → your name → iCloud
- Tap Show All
- Ensure Microsoft Authenticator is switched ON
If Microsoft Authenticator is turned OFF, Microsoft Authenticator iPhone backup will not work. So, be sure to check this setting.
Using Microsoft Authenticator Day to Day
Once these settings are in place, you can use Microsoft Authenticator normally:
- Add your Microsoft work account if 365 MFA is not already configured
- Add any other supported accounts
- Approve sign‑ins as usual
There is nothing else to manage. On an iPhone, backup happens automatically in the background.
What Happens When You Get a New iPhone?
If your phone is lost, damaged, or replaced, restoring Microsoft Authenticator is straightforward:
- Sign in to the same Apple ID on the new iPhone
- Turn on iCloud and iCloud Keychain
- Install Microsoft Authenticator from the App Store
- Open the app
Your Microsoft Authenticator accounts/credentials will reappear automatically. You may be asked to sign in again to some services, but the Authenticator entries themselves are restored. This is why Microsoft Authenticator iPhone backup is so important to set up early.
Hot Tip: Microsoft Authenticator requires iOS 16 or later to work. If Microsoft Authenticator is not available in your App Store inventory, it is usually because your iPhone does not support minimum hardware/software requirements.
Common Questions About Microsoft Authenticator iPhone Backup
Do I need a Microsoft personal account for backup?
- No. On an iPhone, backup uses Apple iCloud only.
Can I choose where the backup is stored?
- No. Microsoft Authenticator iPhone backup always uses iCloud.
Is the backup secure?
- Yes. The data is encrypted and protected by iCloud Keychain.
Summary
For iPhone users, Microsoft Authenticator iPhone backup is simple, automatic, and secure — as long as iCloud and iCloud Keychain are enabled, and iOS is configured to connect Microsoft Authenticator to iCloud. Microsoft does not back up your MFA credentials to your Microsoft 365 account because if you have lost your credentials, you cannot login to 365 to retreive them. Therefore, MFA credentials need to be stored elsewhere.
Google users and Microsoft (personal) account users save their MFA settings in Microsoft (personal) accounts. Click here for guidance to backup 365 MFA settings using Android.
Spending two minutes checking these settings now can save hours of disruption later, and possibly catastrophic loss. For 365 tenancy owners and Global Administrators, this is a critically important utilitiy. If you manage devices or Microsoft 365 for your business and want help configuring this service correctly, Comstat can assist: feel free to get in touch, or use out contact page to organize an appointment which suits your timetable.
You can return to our Index of Articles by clicking here

PC Power Management Explained: Restart vs Shut Down and the Best Daily Power Habits
Restart vs Shut Down and the Best Daily Power Habits
Windows users—and even IT professionals—are unsure how PC power management really works. Two areas cause the confusion: the difference between Restart and Shut Down, and whether you should shut down or sleep your PC at the end of the day. These actions might look similar, but they behave very differently under the hood.
This guide brings both topics together in a simple, practical way to help users of all experience levels take better care of their computers while keeping performance stable and power use efficient.
Click open the headers below to learn more about how best to improve hardware performance with Microsoft’s tools for Windows. You can return to our Index of Articles by clicking here.
Restart vs Shut Down: Why They Are Not the Same
Most people assume that shutting down the PC is the most complete way to reset Windows. Surprisingly, that isn’t true. Thanks to a feature called Fast Startup, a normal shutdown does not clear everything from memory. Windows saves part of the system state to disk so it can boot faster the next time.
This means that using Shut Down often preserves the very problem you might be hoping to fix with a re-boot, whether that’s a misbehaving driver, a glitchy USB device, or a stubborn update. In contrast, Restart always performs a full reset of the Windows kernel, which clears system memory and loads all drivers from scratch.
So, if a user wants a “clean start” to flush out an issue, Restart is the correct choice. Shut down is still useful, but it is not a troubleshooting tool. Understanding this distinction is important, and it helps prevent wasted time and unnecessary frustration.
Daily Habits: Should You Shut Down or Just Sleep the PC?
When the workday ends, many users wonder what to do next: shut down, sleep, or something else? Advice varies wildly, and myths are common. Some people argue that turning the PC on and off wears out hardware. Others insist that leaving it on wastes energy and shortens component life. The truth lies somewhere between the two.
Modern PCs—especially those with Solid State Drives (SSDs)—are designed for frequent power cycling. SSDs do not suffer from mechanical wear caused by spin‑up or spin‑down, which used to be a concern with older hard drives. Components such as processors and RAM also handle start‑stop cycles with ease.
On the other hand, sleep mode is extremely energy‑efficient on modern hardware. A sleeping PC typically uses only a few watts, while allowing you to resume work instantly. This is ideal for office environments where you might take short breaks throughout the day.
Why Microsoft Advises a Policy, Not a Solitary Procedure
A simple rule for good PC power management is:
- Use Sleep during the workday for short or medium breaks
- Use Shut Down at the end of the day if you prefer a fully powered‑off system
- Use Restart whenever the system is unstable or sluggish, or after updates
This approach balances energy conservation, hardware longevity, and overall system reliability—without relying on outdated advice from the mechanical‑hard‑drive era.
Summary
Understanding the difference between Restart, Shut Down, and Sleep helps users make better choices that keep Windows stable and hardware healthy. In modern computing, PC power management is about using each option for its intended purpose:
- Restart for a true clean start
- Shut Down for a full power‑off at the end of the day
- Sleep for convenience and efficiency during regular working hours
Developiong good habits help prevent common issues, improve long‑term performance, and remove the guesswork from everyday PC use. It is true that inexpensive hardware is often built for comparatively limited processor duty cycles in its lifetime, so careful PC power management is especially useful with budget hardware used for critical production jobs.
For more help about improving Windows performance, feel free to get in touch, or use out contact page to organize an appointment which suits your timetable. You can return to our Index of Articles by clicking here

Windows Recovery Drive: Why Microsoft Recommends It
Windows 11 Recovery Drive: A Practical Safety Net, Not an Optional Extra
Microsoft explicitly recommends creating a Windows recovery drive so that your operating system can be repaired or reinstalled if your computer fails to boot, or if it becomes unstable. This guidance exists because some failures cannot be resolved from within Windows itself. Microsoft’s published recommendations are available here.
A Windows recovery drive is not a cure‑all. It will not fix every issue. However, it is one of the simplest and most effective tools for reducing downtime, avoiding data loss, and preventing expensive and prolonged recovery workarounds when things go wrong.
Click open the headers below to learn more about Microsoft’s Windows 11 Recovery Drive. Support options are available for professional assistance. You can return to our Index of Articles by clicking here.
Microsoft recommends Windows Recovery Drive
Microsoft advises users to create a Windows recovery drive as a precautionary measure. This “best practice” reasoning is straightforward. If Windows cannot start, built‑in recovery options may be inaccessible. A recovery drive allows access to advanced startup tools, system repair options, and, if required, a clean reinstallation of Windows.
When created correctly, a Windows recovery drive can also include include system files. This allows you to re-install Windows even if the internal recovery partition is damaged or missing. Unless you can do this, you might have to buy a new Windows license. At worst case, labout costs might mean that is is more economical to buy a new computer.
From Microsoft’s perspective, the recovery drive is part of basic system hygiene. It is comparable to keeping backups or applying security updates. You hope that you will never need it, and if you do, then you are exposed if a Windows recovery drive is not available.
When do I need a Windows Recovery Drive?
A Windows recovery drive is most valuable when normal troubleshooting is no longer possible. Common examples include:
- Windows 11 fails to boot after an update or driver change
- File system corruption prevents access to recovery options
- Windows’ internal recovery partition is damaged or deleted
- Malware or ransomware interferes with system startup
- A replacement SSD or hard drive needs Windows reinstalled
- BitLocker recovery and repair tools are required offline
- Remote support is unavailable and local recovery is needed
In these situations, the absence of a Windows recovery drive often leads to improvised solutions. These take more time, cost more money, and increase the risk of data loss.
Hot tip: while a Windows recovery drive can save significant re-installation/restoration time and costs, users still need to know what edition of Windows and their Microsoft (personal) account credentials to reinstate Windows licensing.
Why Microsoft Advises a Policy, Not a One‑Off Action
Microsoft’s guidance goes beyond simply creating a recovery drive once. For managed environments and serious users, Microsoft recommends a policy‑based approach to recovery.
A proper Windows 11 recovery drive policy answers several practical questions:
- Who creates the recovery drive
- When it is created or refreshed
- Where it is stored
- How it is labelled and tracked
- How it is tested
Without a policy, recovery drives are often outdated, missing, or stored in the same place as the failed device. That defeats their purpose.
A documented approach ensures that recovery remains possible even during staff absence, hardware failure, or time‑critical incidents.
Windows Recovery Drive helps to control and reduce risk
Windows recovery drive does not solve every problem. However, especially as computers near their anticitpated longevity , your Windows recovery drive it plays a critical role in mitigating cost.
When recovery options are limited, support is harder to source and margins for error increase
- Emergency data extraction
- Lengthy rebuilds from scratch
- Extended and unpredictable downtime
These consequences are often far more expensive than the simple act of creating and maintaining a recovery drive. Sometimes, problems like hardware failure in ageing equipment means that there are insufficient resources for Windows to operate properly in the first place. In this kind of situation, a Windows recovery drive cannot restore problems consequential to permanent hardware damage.
However, a Windows recovery drive reduces dependency on complex recovery workarounds which small business users are needlessly exposed to so often. Instead of ad hoc intervention, Microsoft’s recommendation for restoration with a Windows recovery drive provides the best chance for shortening resolution time and restoring control when systems fail in unexpected ways.
Computer Life expectancy affects recovery options
In larger businesses, the average replacement cycle for computers used for desktop productivity is 3-5 years. Self-employed users demand much more from their computers. This kind of profile is more in line with corporate power users, whose computers are replaced at 2.5 – 4 years. This is because this kind of useage imposes a heavier computational duty cycle on hardware. While System Restore and Windows Recovery can help mitigate running costs, these kinds of tools cannot perform when hardware has failed or is reaching the end of its duty cycle.
Summary
Microsoft recommends that compiling a Windows 11 recovery drive because Windows systems do fail, even when well managed. You may never need it. We hope so. But if you do, and the freely available resource is not available, the risk of recoverycosts increase sharply.
Larger business do not use recovery drives because they tend to operate centralised systems that provide a pre defined Windows “mirror”, which can be “pushed” to a compromised workstation. Small businesses and home businesses do not enjoy this kind of support. A Windows recovery drive provides the substitute alternative.
If you would like help implementing a Windows 11 recovery drive policy, or aligning it with your wider Microsoft 365 and device management strategy, feel free to get in touch, or use out contact page to organize an appointment which suits your timetable. You can return to our Index of Articles by clicking here

Why BitLocker for Small Business Matters
Introduction: A common small business risk
BitLocker is an important utility in small office/home office situations. For instance, your laptop is probably your office. The device holds emails, customer details, invoices, and passwords. If that laptop is lost or stolen, the impact on productivity can be serious.
BitLocker is used widely in disciplined business networks and Windows Pro/Windows Enterprise enable the feature by default. However, home users are exposed to the same daily risks that larger business plan for. So, why is this kind of security not enabled be default in Windows Home?
This is because Windows Home is designed for personal rather than business or professional use. Windows Home users are provided with a lite version of BitLocker called “device encryption” to simplify this kind of security. This article helps you understand why this choice is left to user discretion, even though Microsoft recommends BitLocker or device encryption in business or professional contexts regardless of your edition of Windows.
Click open the headers below to learn more about Microsoft BitLocker. Support options are available for professional assistance. You can return to our Index of Articles by clicking here.
What is BitLocker?
BitLocker is built‑in disk encryption in Windows.
Encryption means your data is scrambled so it cannot be read without permission. If someone steals your computer and removes the hard drive, they still cannot read your files when the hard drive is secured this way.
With BitLocker and device encryption this protection happens automatically in the background. You do not need to open files differently or remember extra passwords in daily use for locally stored data. BitLocker or device encryption ensures:
- Protection of customer and client information
- Reduction of legal and GDPR exposure after a loss
- Protection for email, documents, and saved passwords
- Your data is encrypted in absolute terms
For a home office, BitLocker/device encryption is often the single most important security control you can enable.
Why BitLocker is not enabled in Windows Home by default
Windows Home is designed for personal use. Microsoft assumes:
- One main user *
- Personal files
- Lower compliance risk
- Minimal technical setup
* See our notes about Microsoft Windows accounts here.
Because of this, BitLocker is enabled by default for Windows “Pro” and “Enterprise” editions. These editions are aimed at people who:
- Handle business or client data
- Travel with laptops
- May face regulatory obligations
So, device encryption’s default “disabled” state in Windows Home is not a limitation of your hardware. It is a product positioning choice because Windows Home is not designed for professional users.
Does Windows Home use Encryption or BitLocker?
Although Windows Home does not provide the more fully configurable BitLocker available in Windows Pro and Enterprise, it still provides an option for BitLocker “lite”, which is managed by a utility called device encryption, which:
- Uses the same encryption engine as BitLocker
- Encrypts only the main system drive
- Turns on automatically on supported hardware
This can be configured in Settings -> Privacy security -> Device encryption
You can read more about Device Encryption in Windows Home here.
A common misunderstanding about BitLocker and ransomware
Users often worry that BitLocker could be used by criminals to lock them out of their resources, because of past and recent headlines about BitLocker ransomware.
It is true that ransomware can misuse many tools. However, this does not make BitLocker unsafe or unnecessary.
BitLocker protects data when a device is lost, stolen, or powered off. Ransomware is a different problem that requires backups and malware protection.
For small businesses and home professionals, the biggest real‑world risk is still device loss, not advanced cyber attacks. BitLocker and device encryption directly addresses that risk. For instance, if a spent computer is taken to a recycling centre, an encrytped hard drive cannot be accessed by third parties. For a spent computer that is destined for recycling, hard drives should be removed and physically compromised to prevent third parties recovering files and date from the hard drive.
What BitLocker does not replace
BitLocker is important, but it is not everything. You still need:
- good backups
- strong passwords
- up‑to‑date Windows security
- sensible email habits
- a data and file retention policy that is commensurate with purpose
Think of BitLocker as the lock on the office door, not the whole alarm system.
Summary: Is BitLocker worth it for a small business?
BitLocker is not about fear or complexity. It is about realism.
Small businesses are not immune to loss, theft, or mistakes. BitLocker/device encryption for small business and professional home users helps reduce the impact when something goes wrong. This is why it exists, and why Windows Pro includes the feature by default. Consider these eventualities if you lost your laptop today:
- would customer or professional data (including customer/client personal details) be safe?
- would emails be secure from third party access?
- could files be copied by third parties?
If not, device encryption for Windowns Home is worth serious consideration. Better still, upgrading from Windows Home to Windows Pro is often one of the lowest‑cost security improvements a professional users can make.
Remember, even though Microsoft does not force device encryption by default in Windows Home, Microsoft still recommends the utility.
For business users operating workstations at scale, Microsoft provides a planning guide here.
If you would like help implementing a device encryption, or you want to discuss this feature more fully, feel free to get in touch, or use out contact page to organize an appointment which suits your timetable. You can return to our Index of Articles by clicking here.
How to Change Your Email Password in Roundcube Webmail
How to Change Your Email Password using Roundcube Webmail
The easiest and safest way to update or change your email password is through Roundcube Webmail. Roundcube is the Webmail utility you access your email with using a laptop or desktop computer.
You could change your email password using cPanel. Unlike cPanel, which includes advanced server management tools, Roundcube focuses on email functionality. So, managing your email preferences including out-of-office responders, redirects, etc. reduces the risk of accidental changes to your other web server settings while still giving you full control over your account credentials.
When you need to contact us
If you do not know your current password, please contact Comstat Support so we can securely reset it for you.
Click open the headers below to learn how to change your email password.
Step 1: Log in to Roundcube
Using your desktop computer, laptop, or tablet, open your web browser and go to your webmail login page using your browser’s navigation field, not your Google Search field.
Your Webmail URL will depend on the domain name you own. For example, if your domain name you use for your email is “yourdomain.com” you would follow these steps.
- Point your browser to https://yourdomain.com/webmail substituting your own domain name.
- Enter your email address
- Enter your password
- Click “Log In”
Step 2: Access Settings
Once you have succesfully log in to Roundcube, you will either land on your Roundcube home page. You might have configured Roundcube to go straight to your inbox.
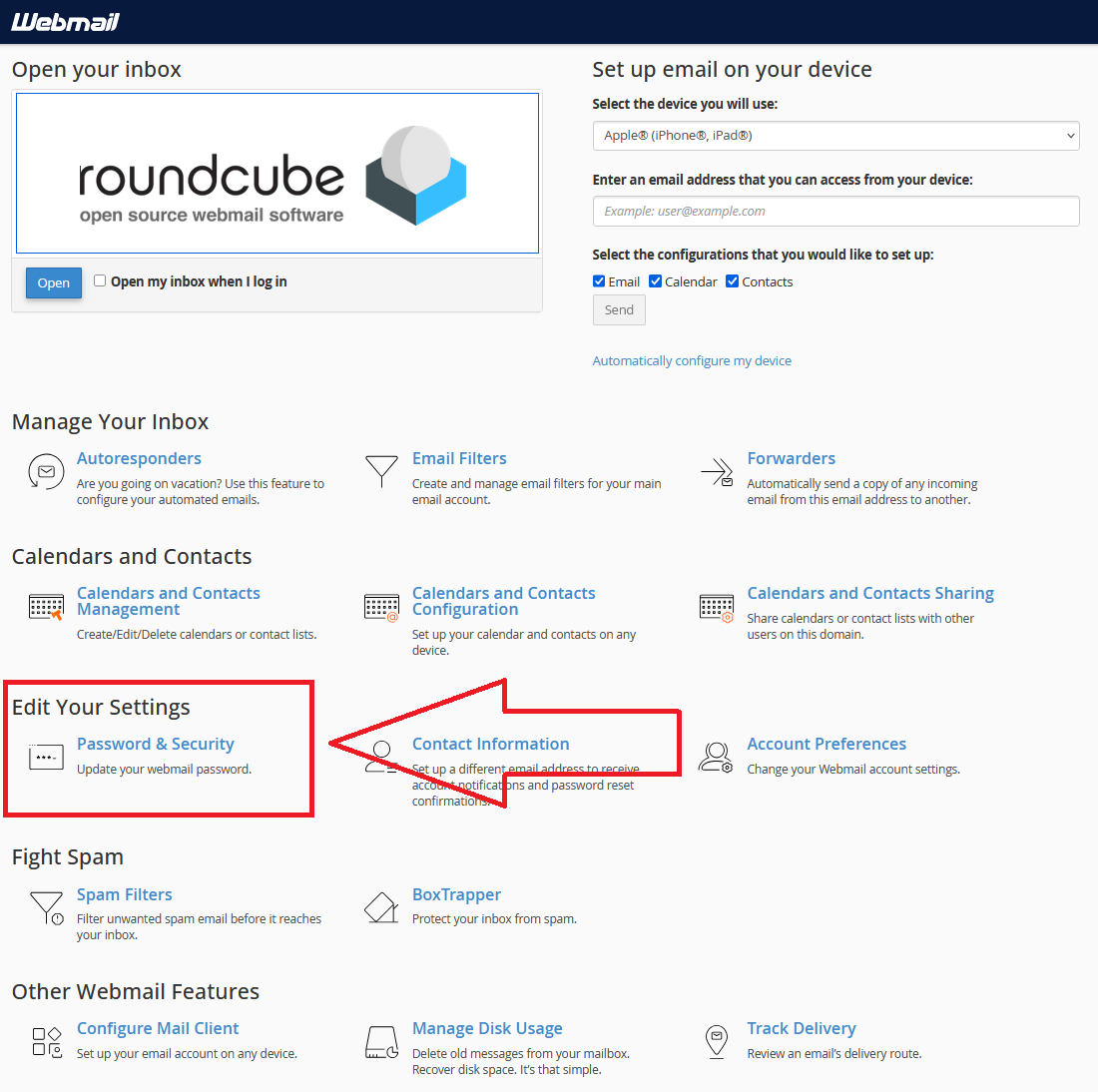
Change your email password using Roundcube Home Page
- Scroll down to <Edit Your Settings>
- Click <Password & Security>
- Change your password
- Click Save or Update
Tip: Use a strong password with uppercase, lowercase, numbers, and symbols. Avoid reusing old passwords.
Change your email password from your Inbox
From the preferences bar on (usually on the left of your Inbox page)
- Click <Webmail Home>
- Scroll down to <Edit Your Settings>
- Click <Password & Security>
- Change your password
- Click Save or Update
Tip: Use a strong password with uppercase, lowercase, numbers, and symbols. Avoid reusing old passwords.
Your Webmail home page includes a fully featured list of utilities, including:
- instructions for configuring email accounts on Windows, Apple, Linux, and Android devices.
- Spam controls.
- Autoforwarding
- email tracking
- much more.
Step 3: Update Your Devices
After changing your password, you will have to modify the password in al the devices that you use to connect to your email account.
Best Practices and Summary
- Change passwords regularly.
- Never share your password.
- • Contact support immediately if you suspect unauthorized access.
Roundcube is a comprehensive email solution and you can find answers to issues here.

Microsoft 365 Global Administrator: Why You Need a Second Admin and How to Assign Roles
Introduction
The Microsoft 365 Global Administrator role is the most powerful role in your tenant. It grants full control over users, groups, and settings. However, many small businesses assume that one global admin is enough—and that this role automatically includes every privilege. In reality, some critical capabilities, such as billing and advanced authentication management, require additional roles. This article explains what a global administrator does, why you need a second Microsoft 365 global administrator, and how to organize roles for maximum security and continuity.
Click open the headers below to learn more about how to protect your IT assets by establishing a second Microsoft 365 Global Administrator to protect your Microsoft 365 tenancy in the event of force majeure. Support options are available for professional assistance.
What Is a Microsoft 365 Global Administrator?
A global administrator in Microsoft 365 (also known as an Entra ID global admin) can manage all aspects of your tenant, including user accounts, licenses, and security settings. This role is essential for tasks such as:
- Adding or deleting users
- Resetting passwords
- Assigning licenses
- Configuring security policies
However, global admin privileges do not automatically include billing or advanced security functions. For example, managing invoices for your tenancy, buying/cancelling licenses, or overriding multifactor authentication (MFA) blocks requires additional separate roles.
Why Is a Seond Micrsoft 365 Global Administrator Is Essential
Microsoft recommends having at least two global administrators. This ensures:
- Business continuity during emergencies
- Shared responsibility for critical changes
- Reduced risk of lockouts caused by lost credentials or MFA issues
Establishing a second Microsoft 365 Global Administrator in your 365 tenancy protects against you against a situation arising that locks you out of server-level administration.
Roles That Complement a Microsoft 365 Global Administrator
To fully mirror the capabilities of your principal Microsoft 365 global administrator, assign these additional roles to the second admin:
- Billing Administrator – Manages invoices, payment methods, and subscriptions
- Privileged Authentication Administrator – Overrides MFA and security blocks
- Authentication Policy Administrator – Configures authentication methods and policies
- Service Support Administrator – Opens support tickets with Microsoft
These roles can be assigned in the Microsoft 365 Admin Center or Azure AD (Entra) under Roles and administrators.
Does Licensing Affect MFA for Microsoft 365 Global Administrators?
No. If a second Microsoft 365 global administrator account does not have a Microsoft 365 license assigned to it, it can still perform MFA authentication. MFA enforcement is identity-based, not license-based. The only limitation is that an unlicensed admin cannot use services like Outlook or Teams. For email alerts and notifications, consider assigning at least an Exchange Online license.
How to Organize Your Admin Accounts
- Create a second global admin account
- Assign MFA to both global admins
- Add complementary roles (Billing, Privileged Authentication, etc.)
- Document your admin strategy for continuity
About ComStat.uk: Internet Service Provider Comstat provides IT support, web hosting, and media services including website design, Microsoft 365 setup, and audio/video production, serving businesses across Denbighshire, North Wales and Wirral from Ruthin, and Lancashire and the Northwest from Bolton.

Microsoft 365 Global Administrator: Why Business Continuity needs 2 global admins
Introduction
For many small businesses, Microsoft 365 is the backbone of daily operations—email, files, collaboration, and security all depend on it. At the heart of this system is the Microsoft 365 Global Administrator, the most powerful role in your tenant. But what happens if the person holding that role leaves suddenly or becomes unavailable? Without planning, this scenario can lead to a catastrophic lockout, halting your business operations. This article explains the risk and how to prevent it.
Click open the headers below to learn more about how to protect your IT assets by establishing a second Microsoft 365 Global Administrator to protect your Microsoft 365 tenancy in the event of force majeure. Support options are available for professional assistance.
The Risk of a Single Global Administrator
When you set up Microsoft 365, the first account created becomes the principal global administrator. This account controls everything: user management, licenses, security settings, and more. If that person leaves the company, passes away, or loses access because their account has been hijacked, your organization could face:
- Inability to renew licenses or update billing details
- Locked-out users due to MFA or security blocks
- No way to add or remove accounts or assign roles
This is not just inconvenient—it can catastrophically disrupt your organization’s IT.
Why a Second Global Admin Is Crucial
Microsoft recommends having at least two global administrators. This ensures:
- Business continuity during emergencies
- Shared responsibility for critical changes
- Reduced risk of lockouts caused by lost credentials or MFA issues
Establishing a second Microsoft 365 Global Administrator in your 365 tenancy protects against you against a situation arising that locks you out of server-level administration.
Best Practices for Setting Up a Second Global Administrator
1. Create a second Microsoft 365 global administrator account
- Use a strong password and enable MFA
2. Assign complementary roles
- Billing Administrator
- Privileged Authentication Administrator
- Authentication Policy Administrator
3. Document access and recovery procedures
- Store credentials securely in a password vault
4. Consider a break-glass account
- A highly secured emergency account with no MFA, monitored for unusual activity.
See our second article in this series to learn more about how network administrators can configure a second Microsoft 365 Global Administrator. Intervention in Microsoft 365, Entra, and and other advanced services can cause catastrophic operational problems so we recommend that you contact us for experienced assistance.
Do I need to buy another 365 license?
No. If your second Microsoft global administrator does not have a Microsoft 365 license, it can still perform MFA and manage the tenant. Licensing only affects access to services like Outlook or Teams—not administrative capabilities.
In our experience, most users lose access to their Microsoft, Apple, and Google accounts via breaches that happen as a consequence of email scams. So, a tenancy owner who operates a solitary Microsoft 365 global administrator user which also handles daily email poses a significant risk.
An unlicensed Microsoft 365 account cannot operate email which helps to protect the account from breach. However, without email, a non-licensed Microsoft 365 global administrator account might not see system-level emails. This is usually not an issue in a small business. In larger businesses, an inexpensive Exchange Online license is assigned to professional network administrators.
Summary
A single Microsoft 365 global administrator is a single point of failure. By adding a second global admin and assigning the right roles, you protect your business from catastrophic lockouts and ensure continuity. See our following article in this series to learn how network administrators configure roles like Billing Administrator and Privileged Authentication Administrator to mirror the principal Microsoft 365 global administrator account.
About ComStat.uk: Internet Service Provider Comstat provides IT support, web hosting, and media services including website design, Microsoft 365 setup, and audio/video production, serving businesses across Denbighshire, North Wales and Wirral from Ruthin, and Lancashire and the Northwest from Bolton.